Setting up a Malware Analysis VM
If you want to start reverse engineering files and scripts it is best to do that in a safe environment. This is where you’ll want to setup an isolated Virtual Machine (aka VM) that will enable you to safely analyze malicious files and scripts. Once you have a VM setup you can start your journey in static analysis land!
Choose your virtualization software
It’s important to note that Hyper-V requires a Windows Profession license. VirtualBox is free and is what I’ll use in this post.
Choose your Operating systen
You can download Windows 7, Windows 8.1 or Windowws 10 VMs from from Microsoft’s Edge Developer downlads here.
I selected MSEdge on Win10 (x64) Stable 1809 on the VirtualBox VM platform and let the download begin. You might as well do something else to keep yourself preoccuiped in the meantime.
I went downstairs to pour myself a a drink. Excuse my typos in advance ;)
Login Information (for Windows Vista, 7, 8, 10 VMs): IEUser, Passw0rd!
Thanks Microsoft! :)))
Importing a VM in VirtualBox
Once the download compeletes unzip the file, I recommend 7Zip, and go make yourself another drink.

Launch VirtualBox and go to File -> Import Appliance… and select the .ova to import.
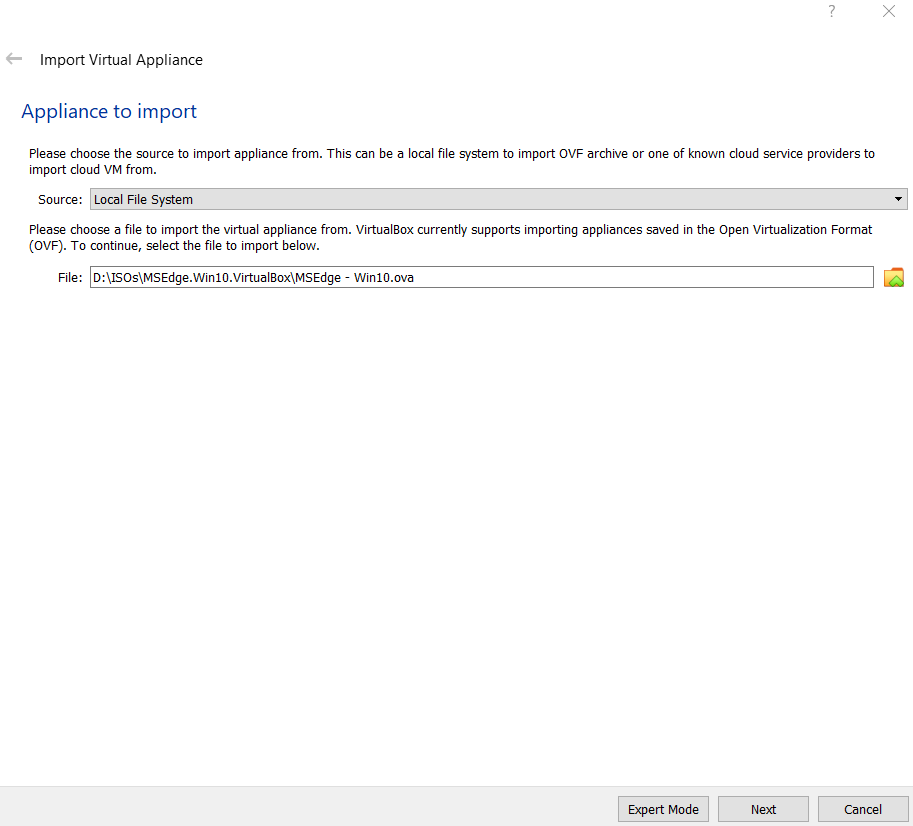
Finalize the VM settings, click Import and go make yourself a snack, popcorn is great, to balance the 2 drinks you had earlier. This process can easily take 10+ minutes.
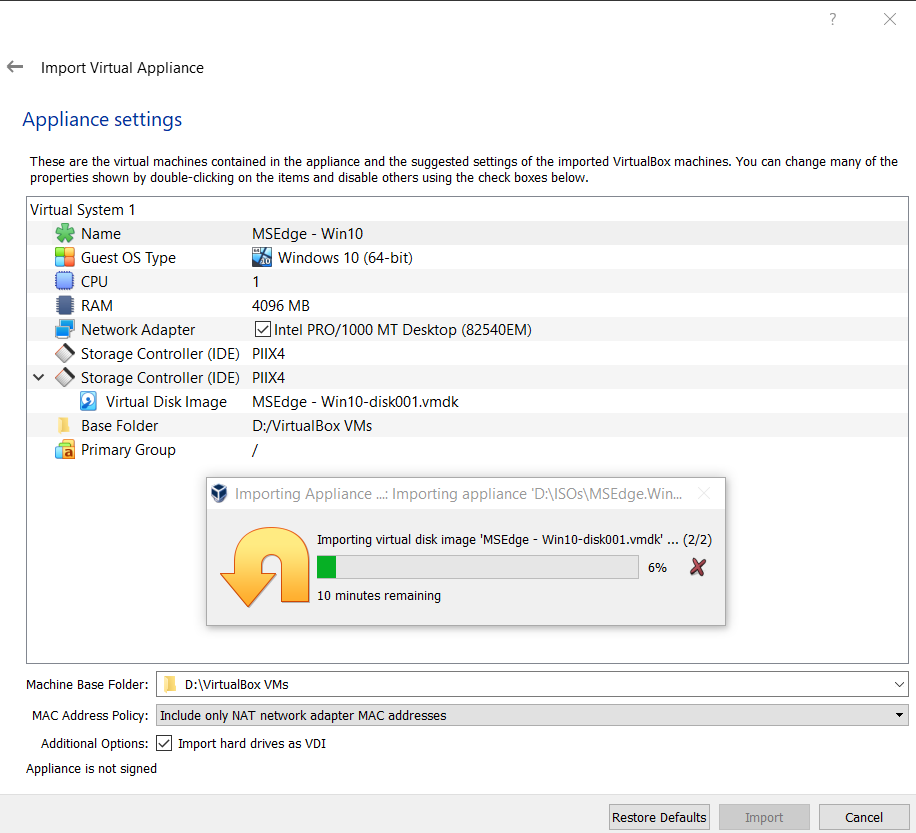
Don’t forget to take a snapshot!
Install VirtualBox Guest Additions
- Before powering on the VM, click on the Settings button and click on the Storage tab.
- Click on the icon that adds an optial drive.
- Click on VBoxGuestAdditions.iso and click on the Choose button.
- Once that is completed power on VM.
- Select Devices -> Insert Guest Additions CD Image.
- If it doesn’t automatically start the installation, open Windows Explorer and click on the CD Drive : VirtualBox Guest Additions.
- Take a snapshot :)
Must have tools used for malware analysis
Now that the Win10 VM has been imported with VirtualBox Guest Additions installed it is time to start it and install malware analysis tools. Here are my favs -
- Debuggers
- OllyDbg
- x64dbg
- Decompilers
- Bytecode-Viewer-2.9.11 (Java)
- DNSpy (.NET)
- Jadx (Java, Android)
- Disassemblers
- Ghidra
- IDA Free
- Frameworks/Runtimes
- Java 11 SDK (Ghidra requirement)
- .NET 4 - 4.8
- Python 2.7 (For those damn legacy scripts)
- Python 3.8 (Preferred)
- Hex Editors
- 010 Editor
- HxD
- Misc tooling
- Sysinternals Suite
- Process Explorer & ProcMon
- RegShot
- Sysinternals Suite
- Network Monitors
- Burp Suite Free Edition
- INetSim
- Wireshark
- PE Inspectors
- CFF Explorer
- DIE (Detect It Easy)
- PE-bear
- pestudio
- Text Editors
- Notepad++
- Sublime Text
You could download each tool individually or use Fireeye’s FLARE-VM automation script https://github.com/fireeye/flare-vm to download the tools mentioned above and more. Eiher downloading each tool and it’s dependencies or running Flare-VM script will take a long time to complete. At least with FLARE-VM the process will be automated for you. Why work harder when you can work smarter?
To get started you will need to launch Powershell as an Administrator, run the command Set-ExecutionPolicy Unrestricted copy the install.ps1 script, https://raw.githubusercontent.com/fireeye/flare-vm/master/install.ps1 to disk and execute it by running .\install.ps1.
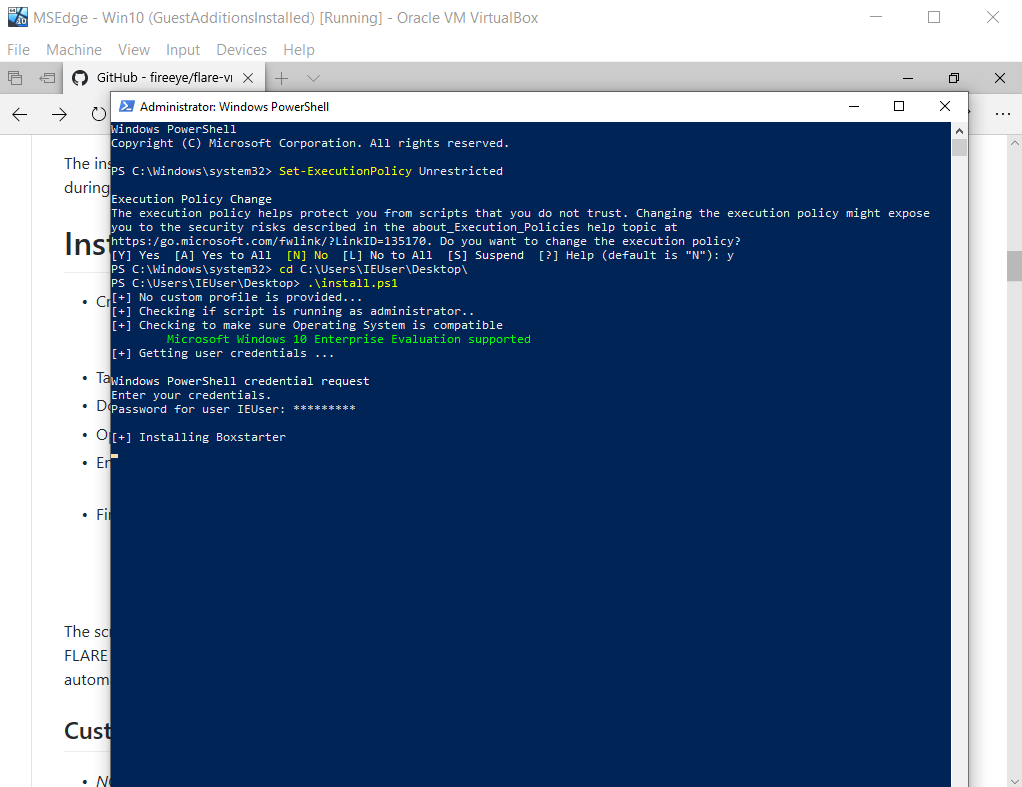
After the script completes, go ahead and take another snapshot.
The Good Stuff
- Shut down the VM.
- Click on the Settings button and click on the Network tab.
- In the Attach to: drop down select Host-only Adapter.
- Power on VM and take a snapshot.
Now you can drag and drop samples you want to analyze in your VM. I choose the sample used in Malware Unicorn’s RE101 workshop found at https://malwareunicorn.org/workshops/re101.html. That concludes the post, you can find some free resources that I recommend you bookmark and reference during your malware analysis journey.
Recommended Resources
- Tips for Reverse-Engineering Malicious Code by Lenny Zelster.
- Malware Unicorn’s RE Workshops.
- CCSF’s CNIT 126: Practical Malware Analysis taught by Sam Bowne.
